IEC 62351 – Cyber Security Series for the Smart Grid
[ ![]() IEC 62351 ] is a series of standards to bring cyber security technologies to some telecontrol protocols.
IEC 62351 ] is a series of standards to bring cyber security technologies to some telecontrol protocols.
On the IEC website there is a detailed introduction into [ IEC 62351 ]. Summarized:
- Standards not only for family of IEC 60870 protocols but also for other telecontrol protocols, covering different protocol layers (Link Layer, Application Layer).
- IEC 62351 standards also define requirements for additional topics, including network and system management, role-based access control (RBAC), cryptographic key management and security event logging.
- Technical specifications for conformance testing are described in standard documents, too.
- A basic principle of IEC 62351 is to reuse existing Internet standards whenever possible to meet the needs to secure Smart Grids.
- The main goals to be achieved with the standards: confidentiality, data integrity, authentication and non-repudiation.
- The freely accessible [ IEC 62351 Glossary ] gives the definitions of terms and acronyms used in the IEC 62351 standards.
You can get the standard documents from different standard organization, e.g. from [ IEC Webstore ].
Here we give a brief overview about the standards IEC 62351-3 and IEC 62351-5 and what and how they are implemented in COMPROTware:Testtool.
IEC 62351-3 (TLS-secured connections)
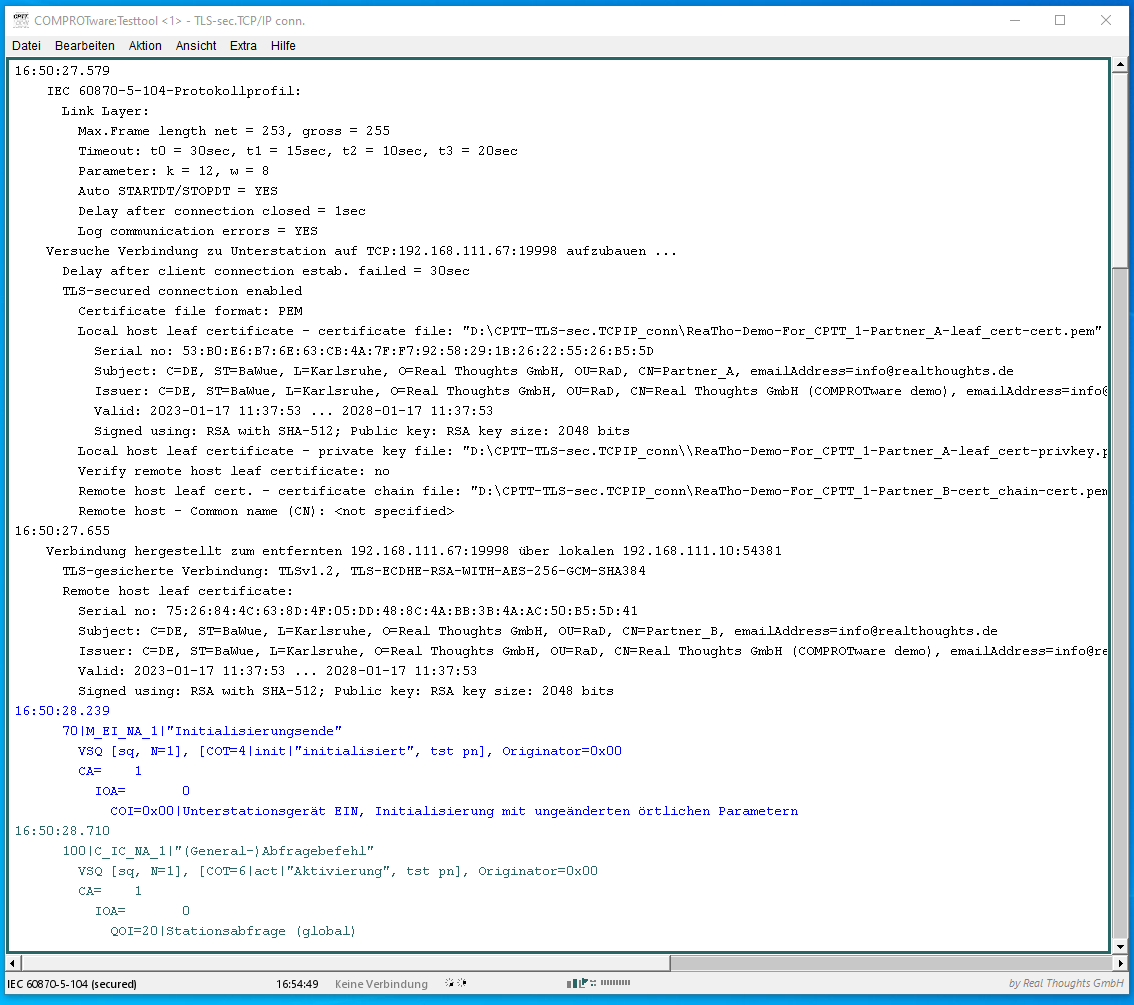
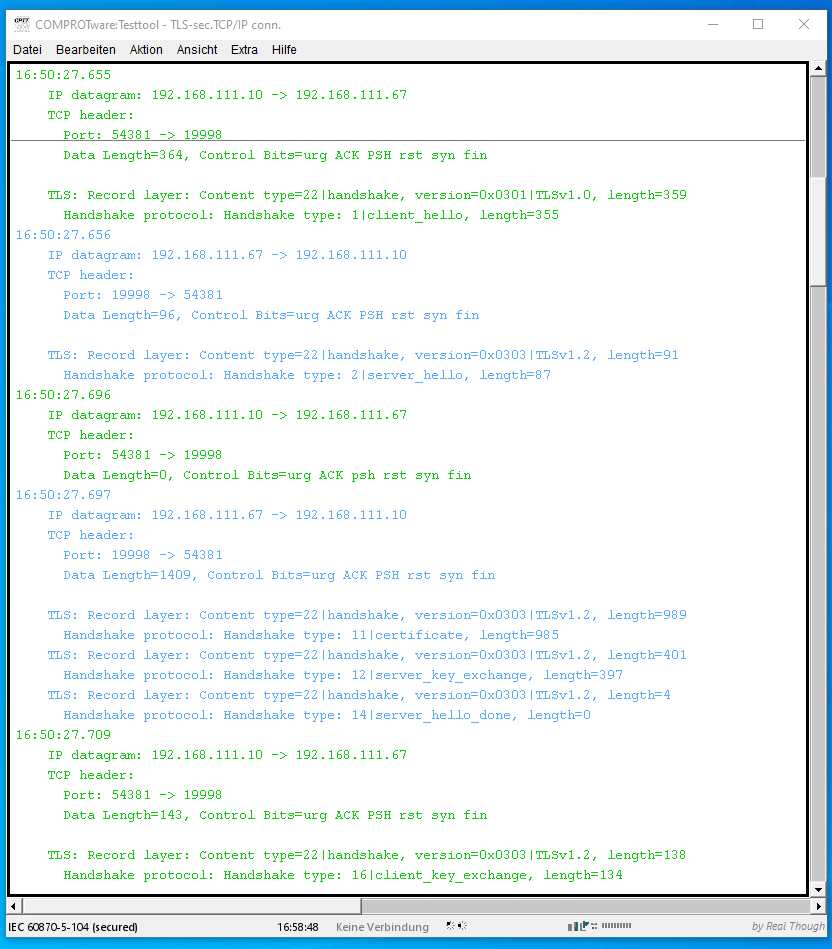
By default there is no authentication nor encryption with telecontrol protocols. To fix this for IEC 60870-5-104, DNP3/IEEE 1815 over LAN/WAN and MODBUS TCP/IP (all three are widely used IP-based telecontrol protocols), TLS-secured connections are used to bring authentication and encryption to these protocols. The idea with IEC 62351-3 is to keep the telecontrol protocol as it is, but to put the telecontrol communication inside a secured connection. TLS-secured connections are well known from the https protocol in web browsers. Basically TLS-secured connections for telecontrol protocols are the same as https connections in the web browser. But with https only the web server is authenticated. With TLS-secured connections for telecontrol protocols the authentication of the client is added to the TLS protocol.
For client and server authentication X.509 certificates are used. For encryption of the telecontrol communication the (steadily evolving) cryptography defined in TLS is used.
Details for TLS-secured connections for IEC 60870-5-104 are laid out in IEC 60870-5-7, for DNP3/DNP3/IEEE 1815 over LAN/WAN in DNP3 SAv5.
These are the standard TCP/IP resp. UDP/IP ports for TLS-secured connections:
- IEC 60870-5-104: TCP/IP port 19998
- DNP3/IEEE 1815 over LAN/WAN: TCP/IP port 19999, UDP/IP port 19999
- MODBUS TCP/IP: TCP/IP port 802
CPTT and IEC 62351-3
For the use of IEC 62351-3 with COMPROTware:Testtool we prepared two documents: Short introduction to TLS/ceritificates as PDF (approx. 120K) and Example with two certificate sets as PDF (approx. 90K) provide a brief introduction to TLS and describe the use of the demo certificates.
CPLB and IEC 62351-3
In COMPROTware:Library (abbrev. CPLB) all Master and Slave implementations of our TCP/IP-based protocol stacks support TLS-secured connections according to IEC 62351-3.
IEC 62351-5 (IEC 60870-5-101/-104 and DNP3/IEEE 1815 protocol enhancements)
The standard IEC 62351-3 uses TLS to secure (authenticate and encrypt) the communication between a Controlling Station and a Controlled Station. In contrast to IEC 62351-3, with IEC 62351-5 the protocol itself is changed. IEC 62351-5 adds user management and authentication on Type
Identification/Function code level.
The standard IEC 62351-3 is limited to network-based protocols, whereas IEC 62351-5 is independant of the physical layer. So IEC 62351-5 is suitable for IEC 60870-5-104 and DNP3 over LAN/WAN but also suitable for IEC 60870-5-101 and DNP3 serial.
For IEC 60870-5-101 and -104 in IEC 60870-5-7 the following additional Type Identifications are introduced:
- S_CH_NA_1 - Authentication challenge
- S_RP_NA_1 - Authentication Reply
- S_AR_NA_1 - Aggressive mode authentication
- S_KR_NA_1 - Session key status request
- S_KS_NA_1 - Session key status
- S_KC_NA_1 - Session key change
- S_ER_NA_1 - Authentication error
- S_UC_NA_1 - User certificate
- S_US_NA_1 - User status change
- S_UQ_NA_1 - Update key change request
- S_UR_NA_1 - Update key change reply
- S_UK_NA_1 - Update key change − symmetric
- S_UA_NA_1 - Update key change − asymmetric
- S_UC_NA_1 - Update key change confirmation
- S_IT_TC_1 - Integrated totals containing time- tagged security statistics
For DNP3 serial and DNP3 over LAN/WAN in DNP3 SAv5 the following Function Codes are added:
- Function Code 32 - Authentication Request
- Function Code 33 - Authentication Request – No Ack
- Function Code 131 - Authentication Response
And these new Object Groups are introduced:
- Object Group 120 - Authentication
- Object Group 121 - Security statistics
- Object Group 122 - Security statistic events
It is noteworthy that with IEC 62351-5 statistical data about the secured connection is also transmitted using the protocol.
CPTT and IEC 62351-5
Currently Real Thoughts is working to add IEC 62351-5 to COMPROTware:Testtool. Are you intested in joining our work in progress? Send us an e-mail: e-mail cptt@realthoughts.de
CPLB and IEC 62351-5
Currently Real Thoughts is working to add IEC 62351-5 to COMPROTware:Library. (abbrev. CPLB) Are you intested in joining our work in progress? Send us an e-mail: e-mail cplb@realthoughts.de